Signature Generation
1. Simple Authentication
Easy to use, quickly pass authentication
Get Token
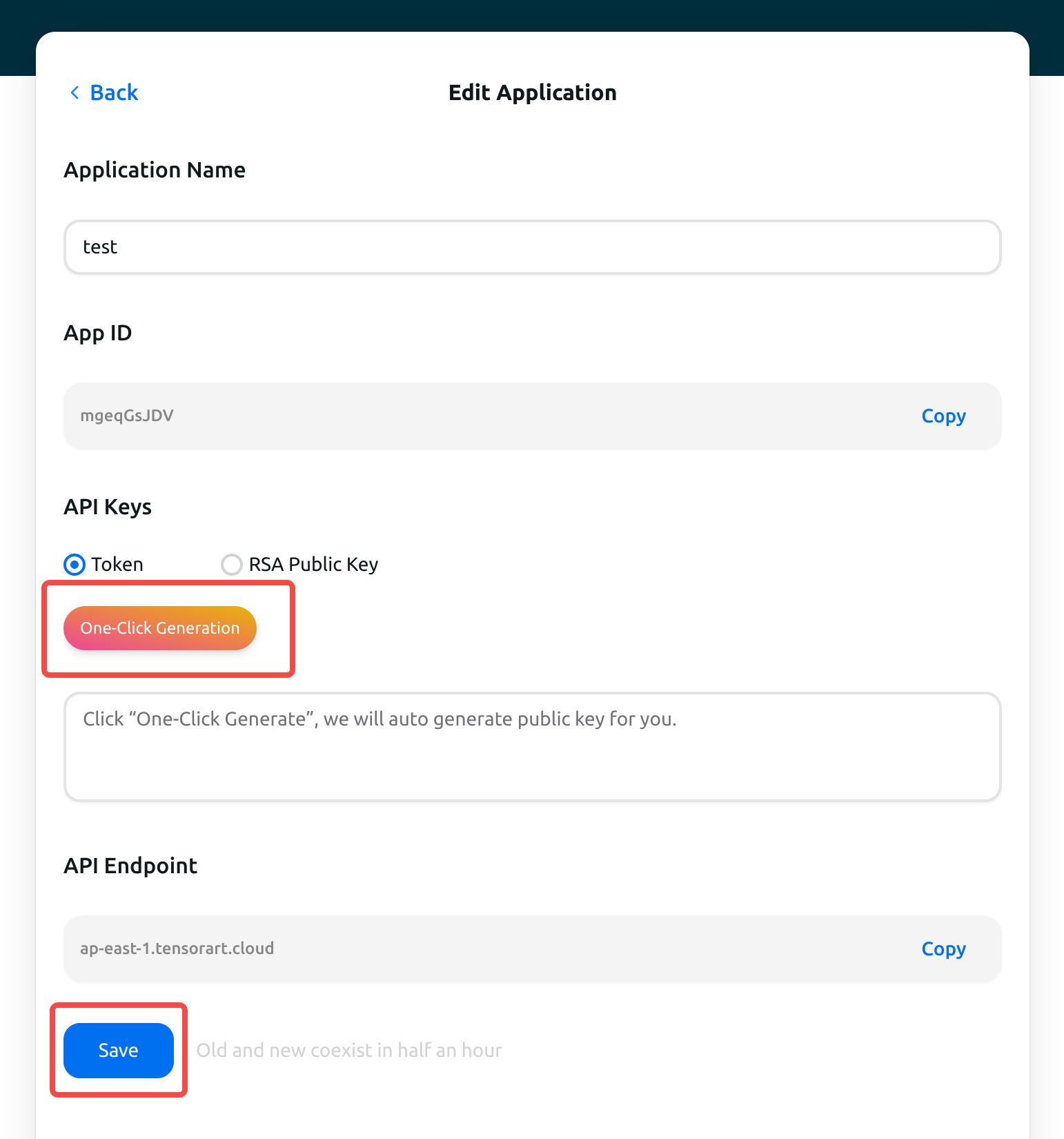
Use Token
To use the token, place it in the "Authorization" field of the request header with the following content:
Bearer {your_token}
Example of a request:
POST https://ap-east-1.tensorart.cloud/v1/jobs
Content-Type: application/json; charset=UTF-8
Authorization: Bearer eW91cl90b2tlbg==
{"request_id":"1562068719690532983734","stages":[{"type":"INPUT_INITIALIZE","inputInitialize":{"seed":-1,"count":2}},{"type":"DIFFUSION","diffusion":{"width":512,"height":512,"prompts":[{"text":"1girl"}],"steps":15,"sd_model":"600423083519508503","clip_skip":2,"cfg_scale":7}}]}
2. Standard Authentication
Better Security, it is recommended to use in a production environment.
Preparation
The application needs to create both a public key and a private key, and upload the public key to the TAMS platform. See Signature Introduction.
Construct the String to be Signed
Example of a request:
POST https://ap-east-1.tensorart.cloud/v1/jobs
Content-Type: application/json; charset=UTF-8
{"request_id":"1562068719690532983734","stages":[{"type":"INPUT_INITIALIZE","inputInitialize":{"seed":-1,"count":2}},{"type":"DIFFUSION","diffusion":{"width":512,"height":512,"prompts":[{"text":"1girl"}],"steps":15,"sd_model":"600423083519508503","clip_skip":2,"cfg_scale":7}}]}
The application's developer constructs the string to be signed according to the specified rules in this document. TAMS will use the same method to construct the string to be signed. If the platform constructs the string to be signed incorrectly, it will result in a failed signature verification. The format of the string to be signed is as follows:
StringToSign =
HTTPRequestMethod + \n +
URL + \n +
RequestTimestamp + \n +
RequestNonce + \n +
RequestBody
- Using the above request example, the HTTP request method is POST, followed by a line break.
POST\n
- The URL of the request is the URL without the domain part, followed by a line break. If the request URL contains query parameters, they should be included as well.
/api/v1/generation?k1=v1&k2=v2
- Get the current system timestamp when making the request. It is the total number of seconds from the Greenwich Mean Time (GMT) 00:00:00 on January 1, 1970 (08:00:00 Beijing Time on January 1, 1970) to the current time. Use it as the request timestamp and follow it with a line break. The API will reject requests that are made too long ago. Please ensure the accuracy of your system's time.
1688985132\n
- Generate a random string for the request nonce, followed by a line break. The nonce should only contain numbers, letters, and hyphens (-). Different requests should use different nonce values. Here, we generate one directly from the command line.
hexdump -n 16 -e '4/4 "%08x" 1 "\n"' /dev/random
5afedaa0150c6abbd78143ed615ab6
5afedaa0150c6abbd78143ed615ab6\n
- Get the request body from the request. Please use the actual JSON body sent in the HTTP request. If the request body is empty, use an empty string.
{
"request_id": "1562068719690532983734",
"stages": [
{
"type": "INPUT_INITIALIZE",
"inputInitialize": { "seed": -1, "count": 2 }
},
{
"type": "DIFFUSION",
"diffusion": {
"width": 512,
"height": 512,
"prompts": [{ "text": "1girl" }],
"steps": 15,
"sd_model": "600423083519508503",
"clip_skip": 2,
"cfg_scale": 7
}
}
]
}
- Concatenate the above parts to construct the string to be signed.
POST
/v1/jobs
1688985132
5afedaa0150c6abbd78143ed615ab6
{"request_id":"1562068719690532983734","stages":[{"type":"INPUT_INITIALIZE","inputInitialize":{"seed":-1,"count":2}},{"type":"DIFFUSION","diffusion":{"width":512,"height":512,"prompts":[{"text":"1girl"}],"steps":15,"sd_model":"600423083519508503","clip_skip":2,"cfg_scale":7}}]}
Compute the Signature
Use the application's private key to sign the string to be signed using SHA256withRSA, and then encode the signature result to Base64 format.
Add the Signature to the HTTP Request Header
The signature is passed through the HTTP Authorization header. The Authorization header consists of the authentication type and the signature information. Authorization: authentication_type signature_info Authorization: authentication_type appid=app_id,nonce_str=request_nonce,timestamp=request_timestamp,signature=signature
- Authentication type (e.g., TAMS-SHA256-RSA, subject to change). ;
- Signature information:
- Application ID: appid
- Request nonce: nonce_str
- Request timestamp: timestamp
- Signature: signature
The values in the signature information are concatenated in the format of key=value, separated by commas (,), without a specific order. Example: *Note that the example may have line breaks due to formatting. The actual data should be in one line.
Authorization: TAMS-SHA256-RSA app_id=20003093682940,nonce_str=5afed
aa0150c6abbd78143ed615ab6,timestamp=1688985132,signature=TPewM7YwG+9S1Vs
55EDcmONsPQn5mltkCjXzXr2mUSn7SGaKD1vggq2Megfhyu3a2SHRBS1g94VRaMFKrVTH
bhNgcV8d26LjLU98Em2w+d+ZrnoG1NVrXSnB1WQJSQeeue4X+giKHFDqpok92p5Yw/IwX
z0u8UaEgXMRJSC3HqfmY4u9zI4YRld4xn7wJIRpn1k0MQ/zTzbZbFDPfYmTEbP6QofvR6G8z
Z19Sx3b2LWvG+RPENGEmFAeB87/NSL3w6P8iGcVJI85iG12jc3shUWK22t/3BXj8bzFGYfV3q
i3f2gXgBd7PsFfNuK9jf//kqKXTevlJu90CZQewidMhg==
Finally, use cURL as an example to send the request:
curl 'https://ap-east-1.tensorart.cloud/v1/jobs' \-H 'Content-Type: application/json' \-H
'Accept: application/json' \-H 'Authorization: TAMS-SHA256-RSA
app_id=20003093682940,nonce_str=5
afedaa0150c6abbd78143ed615ab6,timestamp=1688985132,signature=TPewM7YwG+9S
1Vs55EDcmONsPQn5mltkCjXzXr2mUSn7SGaKD1vggq2Megfhyu3a2SHRBS1g94VRaMFKr
VTHbhNgcV8d26LjLU98Em2w+d+ZrnoG1NVrXSnB1WQJSQeeue4X+giKHFDqpok92p5Yw
/IwXz0u8UaEgXMRJSC3HqfmY4u9zI4YRld4xn7wJIRpn1k0MQ/zTzbZbFDPfYmTEbP6QofvR
6G8zZ19Sx3b2LWvG+RPENGEmFAeB87/NSL3w6P8iGcVJI85iG12jc3shUWK22t/3BXj8bzFG
YfV3qi3f2gXgBd7PsFfNuK9jf//kqKXTevlJu90CZQewidMhg==' \-d
'{"request_id":"1562068719690532983734","stages":[{"type":"INPUT_INITIALIZE","inputInitialize":{"seed":-1,"count":2}},{"type":"DIFFUSION","diffusion":{"width":512,"height":512,"prompts":[{"text":"1girl"}],"steps":15,"sd_model":"600423083519508503","clip_skip":2,"cfg_scale":7}}]}'
Signature Demo
Below are demo implementations of signature generation in various programming languages, making it easy and quick for everyone to use.