Signature Introduction
Ensure the authenticity of the request and the integrity of the data by verifying the signature.
Request signature and verification
When sending request, the application needs to use its own private key to perform SHA-256 with RSA signature on key data combinations such as API URLs and message bodies. The requested signature information is transmitted through the HTTP header Authorization. For specific instructions, please refer to the Signature Generation Guide. Requests that do not carry a signature or fail signature verification will not be executed and will return 401 Unauthorized. The platform will use stored public keys to verify the signature when processing requests. After successful verification, it will return the correct result.
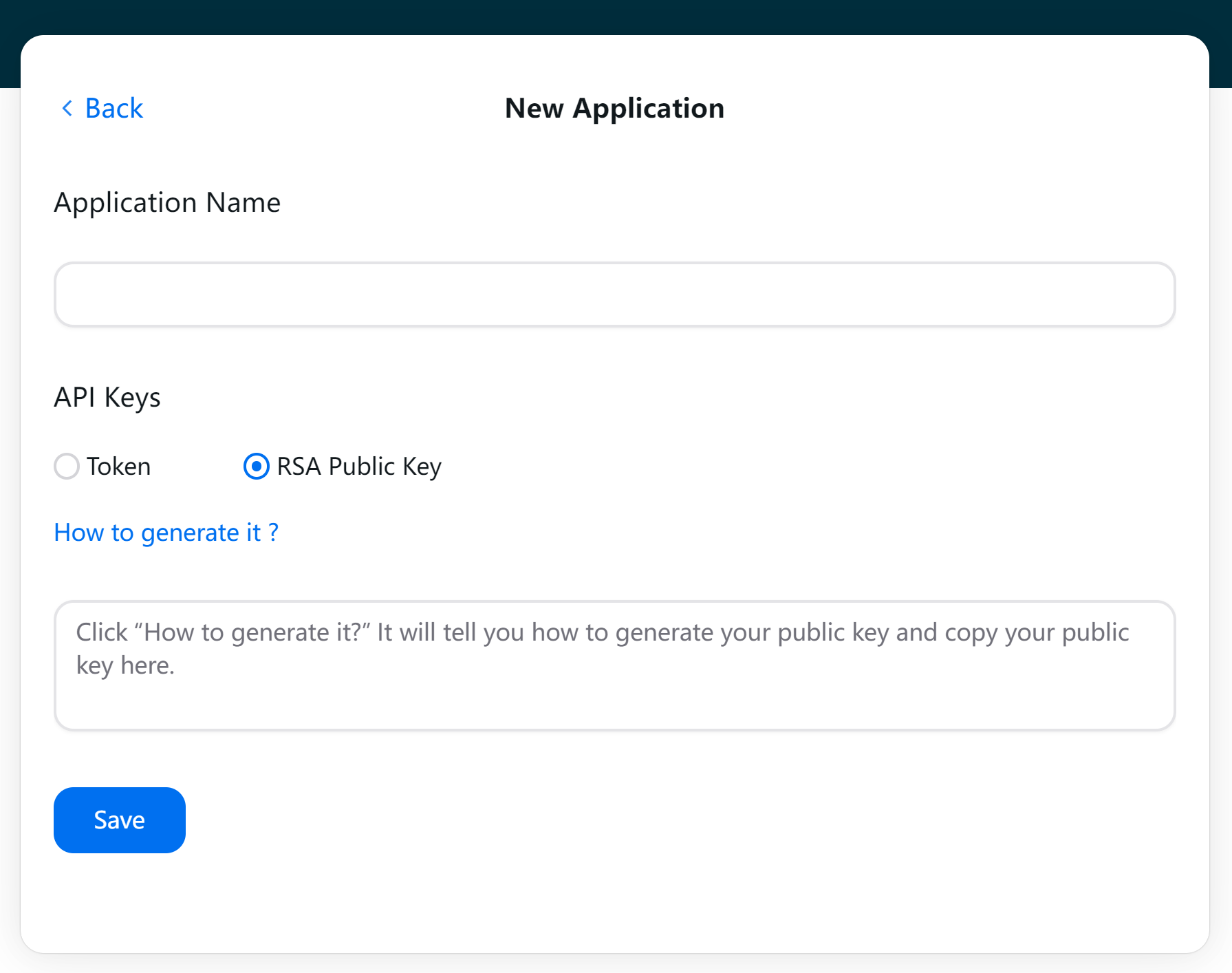
Application private key and public key
The application requires users to generate an RSA private key with a length of 2048 bits or more and export the public key for upload to the TAMS platform.
The following command will generate a 2048-bit PKCS#1 PEM format RSA private key named private_key.pem:
openssl genrsa -out private_key.pem 2048If conversion to PKCS#8 format is required, you can use the following command to export it to private_key_pkcs8.pem:
openssl pkcs8 -topk8 -inform PEM -in private_key.pem -outform PEM -nocrypt -out private_key_pkcs8.pemSometimes conversion to DER format is necessary (e.g., for certain Java packages). You can use the following command to export it to private_key.der:
openssl pkcs8 -topk8 -inform PEM -outform DER -in private_key.pem -out private_key.der -nocryptExport the public key public_key.pem:
openssl rsa -pubout -in private_key.pem -out public_key.pem
Upload the public_key.pem to the TAMS platform or provide it to developers or product personnel. Use private_key.pem or another format of the private key for signing in the code.
Do not expose private key files in public places.